The IP Power Technologies Security Standard (ISS) allows remote access to devices within restricted intranet environments in full security and without compromising firewalls or security policies. ISS overcomes the security issues usually connected to allowing access to device by a third party or from location that are not part of the Intranet:
- how can we be sure that access to the management network's devices is allowed only to accredited users?
- how do we prevent any data exchanged from being useful to potential network intruders?
Two weapons against hackers
ISS contains a powerful combination of a strong authentication mechanism to counter any identity spoofing and a strongly-encrypted communication to make the transmitted data useless to any 3rd party. The combination of both mechanisms guarantees that access to managed devices is truly secure.
Joining the management network
To become part of the management network, any InfraNode or InfraGate must first register itself on the InfraReachServer, which is the only authority in the management network that can guarantee the identity of any manageable device or managing users. This is a one-time-only registration operation requiring the intervention of an authenticated technician. It cannot be repeated twice for the same controller.
The registration process uses a double private/public key mechanism that is implemented using 1024bit-long RSA keys. This is resistant to any practical brute-force cracking, even when done through an internet-distributed application.
The public keys are exchanged between the InfraNode and the InfraReachServer only at this stage and are stored for subsequent use. At registration time the server sends also an RSA message that includes passwords and 128 bits block cypher keys needed for future connections.
The private key remains in the InfraNode's hardware (flash ROM in case of an InfraNode and represents the only way to decode a message encrypted using the corresponding public key: this makes it impossible for anyone else other than the right client to understand the authentication and communication messages.
Strong 1024bit authentication: getting access to the management network
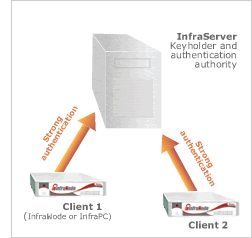
Anytime a client needs to establish a connection to the management network it must re-authenticate itself to the InfraReachServer.
This can be done only by clients that have already registered on the InfraReachServer and so possess the proper keys and passwords.
The authentication process involves sending 1024bit-encrypted RSA messages from the client to the InfraReachServer using several steps involving dynamically changing keys, thus increasing the security in identifying the client.
The secure IP Power Technologies IP link
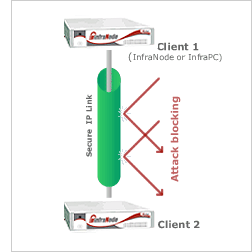 After successful authentication, the InfraNode can establish a communication to the remote management network Infraclient (which has just been re-authenticated by the InfraReachServer as part of the session setup).
After successful authentication, the InfraNode can establish a communication to the remote management network Infraclient (which has just been re-authenticated by the InfraReachServer as part of the session setup).All subsequent communication between Infranode and Infraclient is stream-encrypted using a pair of simmetric keys randomly created for that session by the InfraReachServer. The keys are then destroyed and not used in subsequent sessions.